Technology
Our work in Model Informatics and Verifiable Computation has enabled us to build core technologies that enable trustworthy and verifiable AI deployments. We have developed several breakthrough technologies that form the foundation of many of our products and services. Behavioral Fingerprinting, Verifiable Computation for LLMs are two such technologies available today.
Behavioral Fingerprinting
Behavioral Fingerprinting represents a fundamental breakthrough in AI model identification and verification. Unlike traditional approaches that rely on model weights or architecture, our technology creates unique, verifiable fingerprints based on how models actually behave during inference. This enables unprecedented visibility and control over AI deployments across any environment.
Each AI model exhibits unique behavioral patterns that can be captured and encoded into a compact fingerprint, similar to how DNA uniquely identifies biological organisms. We analyze model behavior during actual inference, capturing the subtle differences in how models process and respond to inputs, creating a comprehensive behavioral profile.
| Model Name | Behavioral Fingerprint |
|---|---|
| deepseek-ai/deepseek-llm-67b-base | 008f:00c2:00fa:01d5:02fb:0414:07ae:645e |
| Qwen/Qwen3-32B | 0033:0043:0065:00a1:00de:015d:03a1:5e7b |
| allenai/OLMo-2-0325-32B-Instruct | 01c6:02a7:037f:0548:076b:0c0f:146f:5767 |
| mistralai/Mistral-7B-Instruct-v0.1 | 0000:0000:0008:0028:00c8:022d:0556:4b25 |
| microsoft/Phi-3-medium-128k-instruct | 0218:031d:03f3:04f7:0704:0bd9:154d:5765 |
| codellama/CodeLlama-7b-Instruct-hf | 016a:01b6:02ab:03ca:04f9:07ba:0f66:65a5 |
Explore Fingerprints Live
See behavioral fingerprints in action! Use our interactive registry demo to explore model fingerprints, compare similarities, and understand how behavioral fingerprinting works in practice.
Try the Registry DemoModel Similarity & Lineage Tracing
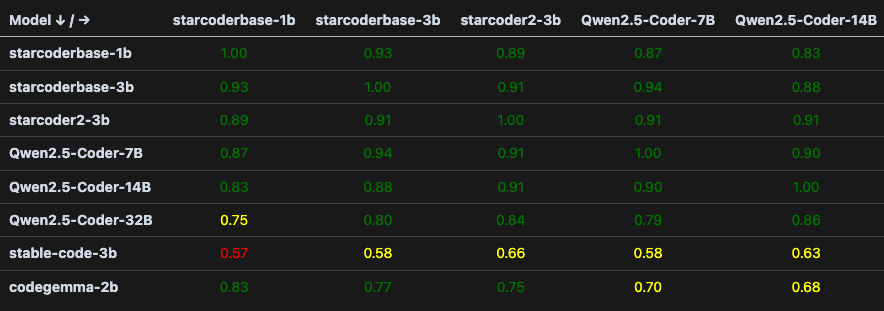
Behavioral fingerprints enable precise similarity analysis between models, revealing relationships and differences that aren't apparent from architecture alone. By measuring behavioral similarity, we can trace the fine-tuning and distillation processes that connect one model to another, providing unprecedented insight into the origins and evolution of AI models.
This capability allows researchers and organizations to understand the lineage of AI models, identify derivative works, and ensure proper attribution and compliance in model development and deployment.
Research Paper: Detecting Chinese Models
Learn more about our research on how to detect if an open source AI model is derived from popular open source Chinese models such as Qwen, DeepSeek, or others.
Download Research PaperVerifiable Computation for LLMs
VAIL collaborated with Daniel Kang and his team at the University of Illinois Urbana-Champaign in the development of ZkTorch, the most efficient zero-knowledge proof system for large, generative AI models. This breakthrough technology enables cryptographic verification of model computations without revealing sensitive model details or training data, ensuring privacy while maintaining verifiability.
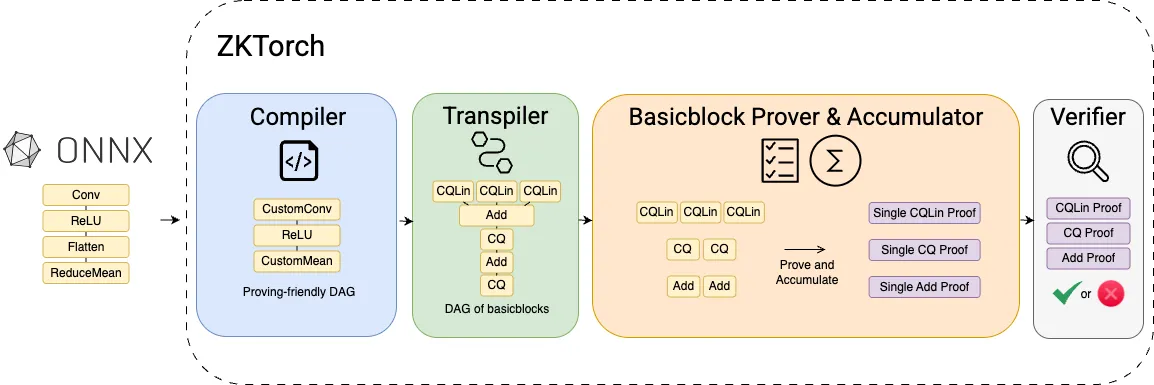
ZkTorch represents a significant advancement in zero-knowledge machine learning, achieving unprecedented performance improvements over existing systems. The system compiles ML models into base cryptographic operations called basic blocks, each proved using specialized protocols, and is built on top of a novel parallel extension to the Mira accumulation scheme.
ZkTorch delivers remarkable performance improvements that make zero-knowledge verification practical for large-scale AI models: 3× smaller proof sizes compared to specialized protocols like Mystique and zkCNN, up to 6× speedup in proving time over general-purpose ZKML frameworks, first end-to-end proof generation for every model in the MLPerf Edge Inference suite v4.1, and support for 61 commonly used ML layers across CNNs, RNNs, and transformers.
By leveraging advanced cryptographic techniques and parallel proof accumulation, ZkTorch allows organizations to prove that specific computations were performed correctly by a particular model without exposing the model's internal workings or the data it was trained on. This creates new possibilities for confidential AI deployments and privacy-preserving verification at scale.
Research Paper
Read the complete ZkTorch research paper to understand the technical details, performance benchmarks, and implementation of this breakthrough zero-knowledge proof system for machine learning.
Download ZkTorch PaperImpact and Vision
These core technologies are revolutionizing how organizations deploy, monitor, and trust AI systems. By providing unprecedented visibility into AI model behavior and enabling model verification, we're ushering in a new era of verifiable and trustworthy AI.